binfalse
ShortCut[xtrlock]: Avoid Xscreensaver
November 30th, 2010By default Xfce provides screen-locking via Xscreensaver. Here is how you change it.
Xfce runs a script called xflock4 to lock the screen, to change the default behavior just foist another script on Xfce!
The default path settings for searching for this executable shows, that /usr/local/bin has higher priority than /usr/bin (here is the original xflock4 located). The rest should be clear!
E.g. to use xtrlock instead of Xscreensaver you just have to link to the binary:
% ln /usr/bin/xtrlock /usr/local/bin/xflock4On a multiuser system you may allow each user to use it’s own locking-solution. So just write a script that checks if $HOME/.screenlock is executable and runs it or falls back to a default screensaver:
#!/bin/bash
# default
DO=/usr/bin/xtrlock
# does user want smth else??
[ -x $HOME/.screenlock ] && DO=$HOME/.screenlock
$DOSave it executable as /usr/local/bin/xflock4 - done…
Homage to floating points
November 22nd, 2010I recently got very close to the floating point trap, again, so here is a little tribute with some small examples!
Because Gnu R is very nice in suppressing these errors, all examples are presented in R.
Those of you that are ignorant like me, might think that 0.1 equals 0.1 and expect 0.1==0.1 to be true, it isn’t! Just see the following:
> a=0.1
> b=0.3/3
> a
[1] 0.1
> b
[1] 0.1
> a==b
[1] FALSEYou might think it comes from the division, so you might expect seq(0, 1, by=0.1) == 0.3 contains exactly one vale that is TRUE !? Harrharr, nothing like that!
> seq(0, 1, by=0.1) == 0.3
[1] FALSE FALSE FALSE FALSE FALSE FALSE FALSE FALSE FALSE FALSE FALSEFurthermore, what do you think is the size of unique(c(0.3, 0.4 - 0.1, 0.5 - 0.2, 0.6 - 0.3, 0.7 - 0.4)) !? Is it one? Not even close to it:
> unique(c(0.3, 0.4 - 0.1, 0.5 - 0.2, 0.6 - 0.3, 0.7 - 0.4))
[1] 0.3 0.3 0.3Your machine is that stupid, that it isn’t able to save such simple numbers ;) And another example should show you how these errors sum up:
> sum=0
> for (i in 1:100) sum = sum + 0.01
> sum
[1] 1
> print(sum, digits=16)
[1] 1.000000000000001As you can see, R tells you that you summed up to exactly one, suppressing the small numerical error. This error will increase with larger calculations! So be careful with any comparisons.
To not fail the next time, for example use the R build-in function all.equal for comparison:
> unique(c(0.3, 0.4 - 0.1, 0.5 - 0.2, 0.6 - 0.3, 0.7 - 0.4))
[1] 0.3 0.3 0.3
> all.equal(0.3, 0.4 - 0.1, 0.5 - 0.2, 0.6 - 0.3, 0.7 - 0.4)
[1] TRUEOr, if you’re dealing with integers, you should use round or as.integer to make sure they really are integers.
I hope I could prevent some of you falling into this floating point trap! So stop arguing about numerical errors and start caring for logical fails ;-)
Those of you interested in further wondering are referred to [Mon08].
References
- [Mon08]
- David Monniaux. The pitfalls of verifying floating-point computations. ACM Trans. Program. Lang. Syst., 30(3):1–41, 2008. http://hal.archives-ouvertes.fr/hal-00128124/en/
ShortCut[R]: locator
November 20th, 2010Welcome to my new category: ShortCut! Here I’ll shortly explain some smart features, unknown extensions or uncommon pathways of going for gold. Today it’s about the Gnu R tool locator.
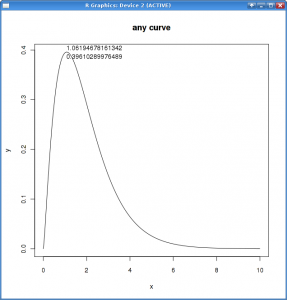
With locator you are able to detect the mouse position inside you plot. Just run locator() and click some points, when you’re finished click the right button and locator will print the x - and y -values of the clicked positions.
With this tool it’s possible to visually validate some numerical calculation.
With a little bit more code, you can output the coordinates right into you plot:
> x<-seq (0, 10, .01)
> plot (x, dgamma (x, rnorm (1, 2, 0.5), rnorm (1, 1, 0.5)), t='l', main='any curve', ylab='y')
> text (p<-locator (1), paste (p, collapse="\\n"), adj=0)With a click into the plot you’ll be able to create a result like figure 1.
RNA-Seq - introducing Galaxy
November 20th, 2010I’m actually attending a lecture with the great name RNA-Seq, dealing with next generation sequencing (NGS). I think the lecture is more or less addressed to biological scientist and people who are working with genome analyzers, but I think there is no harm in visiting this lecture and to get to know the biologists point of view.
These scientists are using different sequencing platforms. Some popular examples are Roche 454, Illumina/Solexa, ABI SOLiD, Pacific Biosciences PacBio RS, Helicos HeliScope™ Single Molecule Sequencer or Polonator, but there are much of more such platforms. If you are interested in these different techniques, you are referred to [Met09]. There is no standard, so all these machines produce output in different formats and quality. In general you’ll get a fastq file as result of sequencing. This file contains roughly more or less small reads of sequences and a quality score of each recognized nucleotide. The quality score is encoded in ASCII characters and contains four line types. Here is an example of such a file:
@SRR039651.1 HWUSI-EAS291:8:1:1:356
TTTTGGTTTTANTTTTTAATAGGTAAATNNNNNNNT
+
BCCBAABCCC=!/=BCABB%%%%%%%%%!!!!!!!%
@SRR039651.2 HWUSI-EAS291:8:1:1:410
TGGTTTGGTTGNTATTGTGATGTATTTANNNNNNNT
+
BBB?@BBB@A0!0<B?.4B?BA?%%%%%!!!!!!!%
@SRR039651.3 HWUSI-EAS291:8:1:1:1018
TTAGTAGTGTTNGTAGAATTTTATTTGTNNNNNNNT
+
BBBB;AB?B@=!,5@B=@ABBB=B%%%%!!!!!!!%As you can see, in general the file contains an identifier line, starting with @ , the recognized sequence, a comment, starting with + , followed by the quality score for each base. It’s a big problem that there is no common standard for these quality scores, they differ in domain depending on the sequencing platform. So the original Sanger format uses PHRED scores ([EG98] and [EHWG98]) in an ASCII range 33-126 ( ! - ~ ), Solexa uses Solexa scores encoded in ASCII range 59-126 ( ; - ~ ) and with Illumina 1.3+ they introdused PHRED scores in an ASCII range 64-126 ( @ - ~ ). So you sometimes won’t be able to determine which format your fastq file comes from, the Illumina scores can be observed by all of this three example. If you want to learn more about fastq files and formats you are referred to [CFGHR10].
Interested readers are free to translate the ASCII coded quality scores of my small example to numerical quality scores and post the solution to the comment!
There is a great tool established to work with these resulting fastq files (this is just a small field of application): Galaxy. It is completely open source and written in Python. Those who already worked with it told me that you can easily extend it with plug-ins. You can choose wheter to run your own copy of this tool or to use the web platform of the Penn State. There’s a very huge ensemble of tools, I just worked with a small set of it, but I like it. It seems that you are able to upload unlimited size of data and it will never get deleted!? Not bad guys! You can share your data and working history and you can create workflows to automatize some jobs. Of course I’m excited to write an en- and decoder for other data like videos or music to and from fastq - let’s see if there’s some time ;-)
But this platform also has some inelegance’s. So there is often raw data presented in an raw format. Have a look at figure 1, you can see there is a table, columns are separated by tabs, but if one word in a column is much smaller/shorter as another one in this column this table looses the human readability! Here I’ve colorized the columns, but if the background is completely white, you have no chance to read it.
So instead of getting angry I immediately wrote a user-script. It adds a button on the top of pages with raw data and if it is clicked, it creates an HTML table of this data. You can see a resulting table in figure 2. If you think it is nice, just download it at the end of this article.
All in all I just can estimate what’s coming next!
References
- [CFGHR10]
- Peter J. A. Cock, Christopher J. Fields, Naohisa Goto, Michael L. Heuer, and Peter M. Rice. The Sanger FASTQ file format for sequences with quality scores, and the Solexa/Illumina FASTQ variants. Nucleic Acids Research, 38(6):1767–1771, April 2010. http://nar.oxfordjournals.org/content/38/6/1767.abstract
- [EG98]
- Brent Ewing and Phil Green. Base-Calling of Automated Sequencer Traces Using Phred. II. Error Probabilities. Genome Research, 8(3):186–194, March 1998. http://www.ncbi.nlm.nih.gov/pubmed/9521922
- [EHWG98]
- Brent Ewing, LaDeana Hillier, Michael C. Wendl, and Phil Green. Base-Calling of Automated Sequencer Traces Using Phred. I. Accuracy Assessment. Genome Research, 8(3):175–185, March 1998. http://www.ncbi.nlm.nih.gov/pubmed/9521921
- [Met09]
- Michael L. Metzker. Sequencing technologies — the next generation. Nature Reviews Genetics, 11(1):31–46, December 2009. http://www.nature.com/nrg/journal/v11/n1/full/nrg2626.html
Resort search results in SquirrelMail
October 23rd, 2010Apart from an IMAP/POP service we provide a webmail front end to interact with our mail server via SquirrelMail. This tool has a very annoying feature, search results are ordered by date, but in the wrong way: From old to new!
SquirrelMail is a very simple to administrate front end, not very nice, but if my experimental icedove doesn’t work I use it too. Furthermore we have staff members, who only use this tool and aren’t impressed by real user-side clients like icedove or sylpheed.. What ever, I had to resort these search results!
Searching for a solutions doesn’t result in a solution, so I had three options: Modifying the SquirrelMail code itself (very bad idea, I know), providing a plugin for SquirrelMail, or writing a userscript.
Ok, hacking the core of SquirrelMail is deprecated, writing a plugin is to much work for now, so I scripted some JavaScript.
The layout of this website is lousy! I think the never heard of div’s or CSS, everything is managed by tables in tables of tables and inline layout specifications -.-
So detecting of the right table wasn’t that easy. I had to find the table that contains a headline with the key From :
var tds = document.getElementsByTagName ('td');
var table = 0;
for (var i = 0; i < tds.length; i++)
{
if(tds[i].innerHTML.match(/^\\s*<b>From<\\/b>\\s*$/))
{
table = tds[i].parentNode.parentNode;
break;
}
}If I’ve found such a table, all the rows have to be sorted from last to first. Except the first ones defining the headline of that table. So I modified the DOM:
if (table)
{
var old = table.cloneNode (true);
var tru = false;
var oldi = old.childNodes.length - 1;
var tablelen = table.childNodes.length;
for (var i = 0; i < tablelen; i++)
{
// don't sort the head to the end...
if (!tru)
{
if (table.childNodes[i].innerHTML && table.childNodes[i].innerHTML.replace(/\\n/g,'').match (/<b>From<\\/b>.*<b>Date<\\/b>.*<b>Subject<\\/b>/))
tru = true;
continue;
}
table.replaceChild (old.childNodes[oldi--], table.childNodes[i]);
}
}Ok, that’s it! Using this script the search results are ordered in the correct way. Let’s wait for a response from these nerdy SquirrelMail-user ;-)